Active Directory Domain Service
Saif Chhipa
12/21/20247 min read
Learning Objective
Active Directory
What is Partition and Components
Global Catalog
Security Groups
Schema
OUs
Tree vs Forest vs Site
FSMO
What is AD DS?
AD DS is a specialized type of database, it is configured on a server and it provides authentication, and resources to the authorized clients or computers.
It stores information about users, computers and services. AD DS stands for Active Directory Domain Service.
AD DS requires one or more domain controllers, each domain controller holds a copy of the database, which continuously synchronizes. All of these controllers can provide authentication and authorization.
Different roles can be assigned to these multiple domain controllers using FSMO.
Multiple DC don’t always means there is a FSMO role define, it can be just for redundancy or better performance.
Domain Controller: A DC is a server that has the AD DS role installed on it.
Member Server: Server which doesn’t have AD role on it and managed by a DC on a network
Domain: Container that hold information about all network resources.
Every resource is called an object.
Domain
Domain can be thought of a workspace where you have/create all your notes and tasks. Under domain you can create and manage Users, Groups, and Computers. It is an Administrative & Replication boundaries for users and computers that are stored in a common directory database
Organizational Units (OUs)
Under domain we can have Organizational Units (OUs). OUs are used to logically group resources of a certain site, department, or a team. For example, you can group all user accounts in the Accounting department under a single OU to apply group policies and permissions efficiently.
Schema
Schema is a blueprint that specifies how data is or will be stored in a database. In Active Directory, it specifies how the data is stored in the NTDS.dtl (New Technology Directory Service: Data Transaction Log) file.
It defines types of objects can exist, such as users, computers as well as the attributes associated with the objects such as name, password and email.
In context of databases, schema defines how the data or the information is structured in a database, for example SQL will have a different structure than Mongo DB.
We can define our schema using the simplest JSON format. For example, if I have JSON with Username and Password as data
The schema will look like this, showing the data structure in my JSON file.
$schema, It tells validators which version of the schema draft to use when processing the schema
Run: regsvr32 schmmgmt.dll -> Run: mmc ->File-> add/remote Snap-in-> add Active Directory Schema
regsvr32 schmmgmt.dll command is used to register a file which is a Snap-In. Executing this command will enable you a GUI inside MMC (Microsoft Management Console) to view and manage the Schema configuration.
Without running this command the Snap-In won’t be visible in MMC.
Snap-In is a software component in MMC that adds management capabilities via user interface. It enables a nice GUI for you.
Core Protocols & Components of AD DS
Active Directory Partition
A partition is a potion of the AD DS database. It is a one single file but it has logical partitions. Each partition contain different data. The 4 partitions are:
Schema Partition
Stores Schema
Configuration Partition
It holds information about AD environment, it has details about sites and replication configuration
Domain Partition
This where all the defined objects are stored, such as computers, users, and groups. Each domain has its own domain partition, and in redundant DC environment, this data is replicated among DCs
Application Partition
Application Specific data, For example DNS exchange.
AD DS Physical Components
- NTDS
- DNS
- Kerberos
- LDAP
LDAP
Lightweight Directory Access Protocol (LDAP) is a software protocol used to query and manage directory information. It allows clients to access directory services, such as Active Directory, to retrieve and manipulate data about users, groups, and other resources.
LDAP is logically linked to the Global Catalog (GC). For example, if a user in China attempts to log in, the LDAP protocol queries the directory to find the closest GC server. This server can then authenticate the user by providing the necessary information efficiently.
That being said, LDAP is also used to query/find information, such as searching for a specific object like a folder using a name if the exact location of OU is unknown.
LDAP supports SSL/TLS encryption and uses cryptographic hashes for passwords. It can be deployed on multiple DCs for better results.
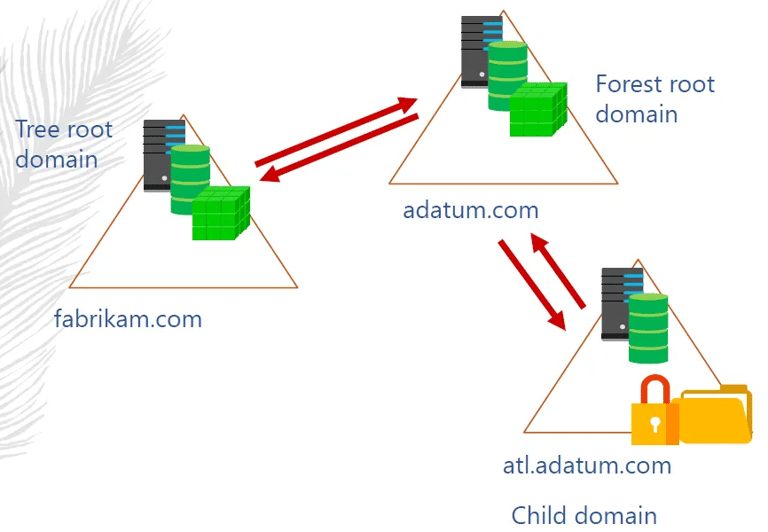
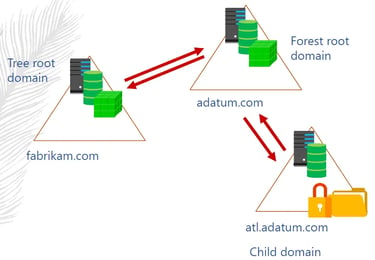
Domain Tree
Collections of domains that are grouped together in hierarchical structures and that share a common root domain. The first DC of a network is the Root domain. All DCs in a tree can have two-way trust.
- All domains in a single tree use the same schema for all types of common objects.
- All domains use the same Global Catalog.
- Each domain in a tree is a separate security entity with its own separate Group Policy settings, permissions, and user accounts.
- Unlike OUs, subdomains in a tree do not inherit permissions and policies from their parent domains.
Forest
Forests are Collections of domain trees that share a common AD DS. For example skynet.com and nuclues.net can share a common AD DS root.net
When you create the first domain on an Active Directory network, you are creating a new forest, and that first domain becomes the forest root domain.
Sites
Site is TCP/IP based container within Active Directory that linked to IP subnets.
Reflects one or more interconnected subnets
Is used to enable a client to access the DC that is physically closest
Is used for DC replication
Reflects the physical aspect of the network
Is composed of only two types of objects, servers and configuration objects
Enable a client to access network servers using the most efficient physical route.
DC replication is most efficient when Active Directory has information about which DCs are in which locations. One advantage of creating a site is that it sets up redundant paths between DCs
Paths are used for replication
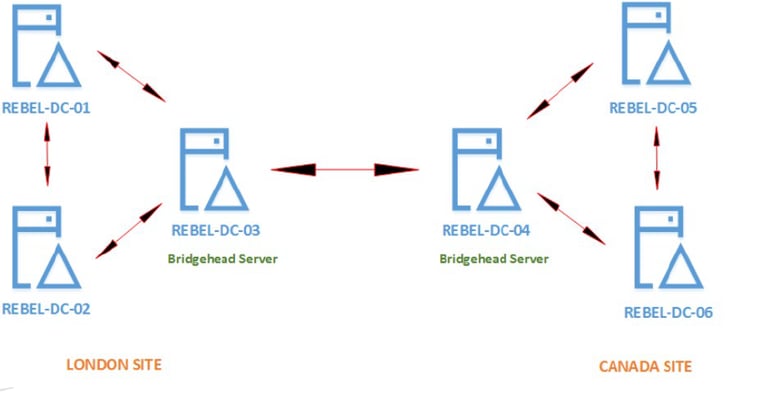
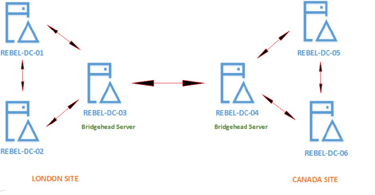
Bridgehead server
A DC that is designated to have the role of exchanging replication information.
Only one bridgehead server is set up per site.
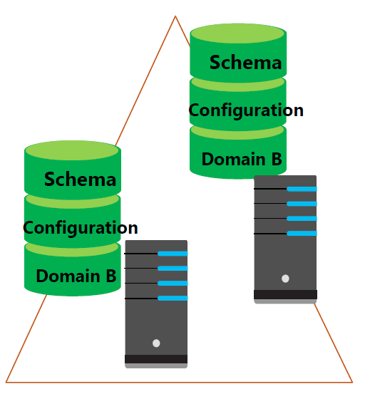
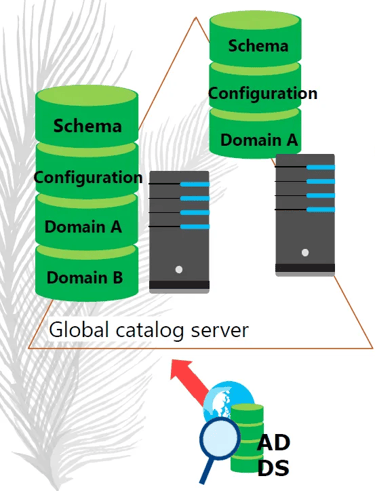
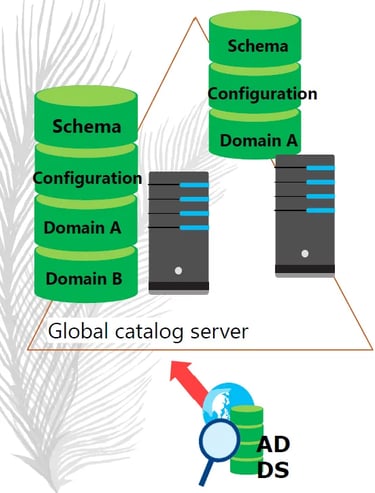
Global Catalog
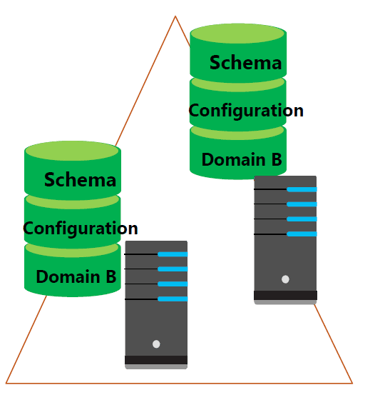
GC server hosts a partial attribute set for other domains in the forest (The partial copy of all objects is used for logon, object searches, and universal group membership). If a Global Catalog server is unavailable, logons that require universal group membership validation will fail.
Supports queries for objects throughout the forest.
Generally, there are 2 GC servers used.
Security Groups & Best Practices
Group Types
Distribution Group
Distribution groups are used solely for email distribution. It doesn’t provide any security, permission for resource access.
Email Distribution: It allow you to send emails to multiple recipients by addressing emails to the group.
Multiple groups can be created and emails can be separately sent to each groups.
It doesn’t have a Security Identifier.
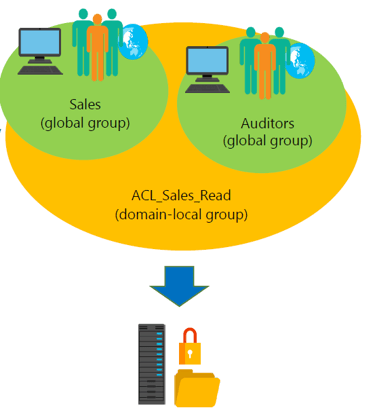
Security Group
Security groups are the common groups we work with, such as admin group, ACIT group.
SGs has unique Security Identifiers which enables the ability to assign permissions to each groups allowing you to have separate security entities.
Group Scope
Local Groups: Can contain Objects, Global Groups, Domain Local groups and Universal groups from the same domain, domains in the same forest and other trusted domain and can be given permissions to resources on the local computer only.
Domain Local Group: Can contain Objects, Global Groups, other Domain Local Groups and Universal Groups from the same domain, domains in the forest and other trusted domains and can be given permission to resources anywhere in the domain.
Global Group: Can only contain Objects and other global groups from the same domain and can be given permission to resources in the domain or any trusted domain (No Domain Local)
Universal Group: Can contain Objects, Global Groups and other Universal Groups from the same domain or domains in the same forest and can be given permissions to any resource in the forest (No Domain Local)
Domain Local
Objects
Global Group
Universal Group
Domain Local (same)
Universal Group
Objects
Global Group
Universal Group (same domain or forest)
Global Group
Objects
Global Group (same domain)
For better security always assign permissions to Domain Local
IGDLA
The best practice for nesting groups is known as IGDLA
Identities: Computers, Users
Global Groups: Such as Sales Group
Domain Local Group: Sales Intern
Assigned: Assigned access to resources

Flexible Single Master Operation
FSMO is a set of rules in Active Directory that help manage the directory. This is very helpful in an environment which includes multiple domain controller. It does that by separating or allocating certain roles to specific domain controller.
FSMO domain controllers or controllers following FSMO rules are specialized DCs that perform certain tasks that can be handled by a single DC in multi-master environment.
The 5 FSMO roles are
Primary Domain Controller Emulator
PDC emulator manages the password change requests and account lockout. It is also used for Time Synchronization. Accurate time synchronization is critical for Kerberos authentication.
By default, PDC synchronize time with a NTP server and ensure that all DCs in the domain are synchronized.
Schema Master
The Schema Master manages schemas across the network. It ensures that all DCs within the forest use the same schema.
The schema master FSMO role holder is the DC responsible for performing updates to the directory schema.
This DC is the only one that can process updates to the directory schema. Once the Schema update is complete, it's replicated from the schema master to all other DCs in the directory. There's only one schema master per forest.
Relative Identifier Master
This role allocates pools of relative identifiers (RIDs) to domain controllers in a domain. Each domain controller uses these RIDs to create unique security identifiers (SIDs) for objects. There is one RID Master per domain.
Domain Naming Master
This role controls the addition and removal of domains in the forest. It ensures that domain names are unique within the forest.
Infrastructure Master (AD Users and Components)
Cross-Domain References: The Infrastructure Master role is responsible for keeping track of references to objects in other domains. For example, if a user in Domain A has permissions to access resources in Domain B, the Infrastructure Master ensures that this cross-domain reference is accurate and up-to-date.
Object Updates: When objects (like users or groups) are moved or renamed in one domain, the Infrastructure Master ensures that any references to these objects in other domains are updated accordingly.
The Infrastructure Master (IM) role should be held by a DC that is not a Global Catalog server(GC).
If the Infrastructure Master runs on a Global Catalog server it will stop updating object information because it does not contain any references to objects that it does not hold.
This is because a Global Catalog server holds a partial replica of every object in the forest.
As a result, cross-domain object references in that domain will not be updated and a warning to that effect will be logged on that DC's event log.
Reference: https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/fsmo-roles