AquaSentinel Project
Saif Chhipa, Deval Malhotra, MD Jahin
20/05/2025 • 5 min read
Part of the project was to deploy a practical IT and OT converged network and conduct vulnerability assessment and penetration testing. The goal was to break into the company's network and hijack the control system (water-level tank).
Under normal conditions, the plant maintains a level of 200mm, achieved by our Allen Bradley PLC using PI (Proportional & Integral) control.
The AquaSentinel project was part of the INCS Culminating project during my time at BCIT. This project integrates my knowledge and skills in Networking, Control Systems, and Defensive & Offensive security.
This project simulates an industrial environment featuring a water-level tank, an Endress+Hauser transmitter, an Allen-Bradley PLC, and a Safety Instrumented System (SIS).
In addition to the Operational Technology (OT) network, we also have an Information Technology (IT) network that includes Domain Controllers (DC), employees' workstations, corporate websites, and other public services.
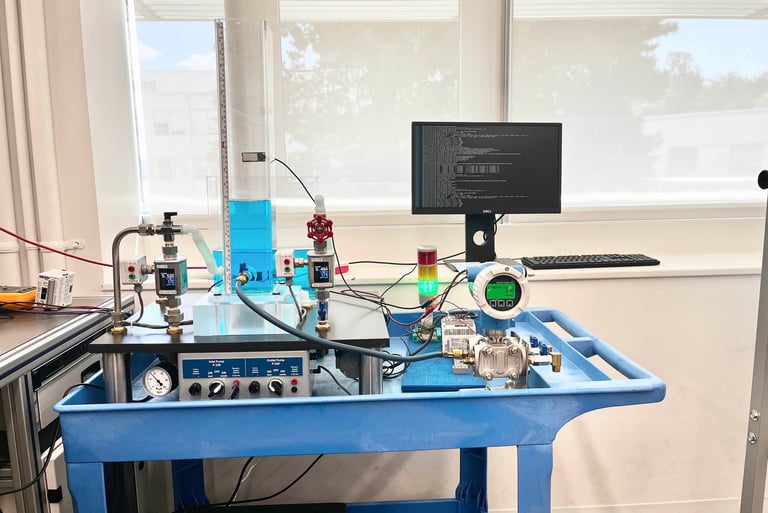


After successfully taking control of the "Plant," my team submitted a proposal to address the identified vulnerabilities and secure the company's network. This approach aims to prevent future attacks, and in the event of a zero-day attack, the system can be decontaminated efficiently.
The security measures include:
Reviewed Network Diagram
Application Control
Intrusion Detection and Prevention Systems
Endpoint Detection & Response
Security Information & Event Management
Honeypots
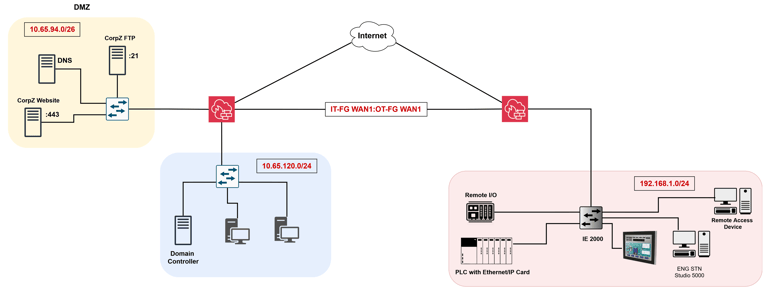
The attackers (my team) would first exploit the company website to collect employee usernames and passwords from the database. In addition, the company's FTP server was exploited and used as the initial access point to the company's network. Attackers began by identifying the running services in the IT network and exploited weak firewall policies. These firewalls lacked proper "Application Control" configurations, allowing the attackers to move laterally within the network. This movement helped them gain further insights into the network and find ways to exploit it.
Initial Network Topology
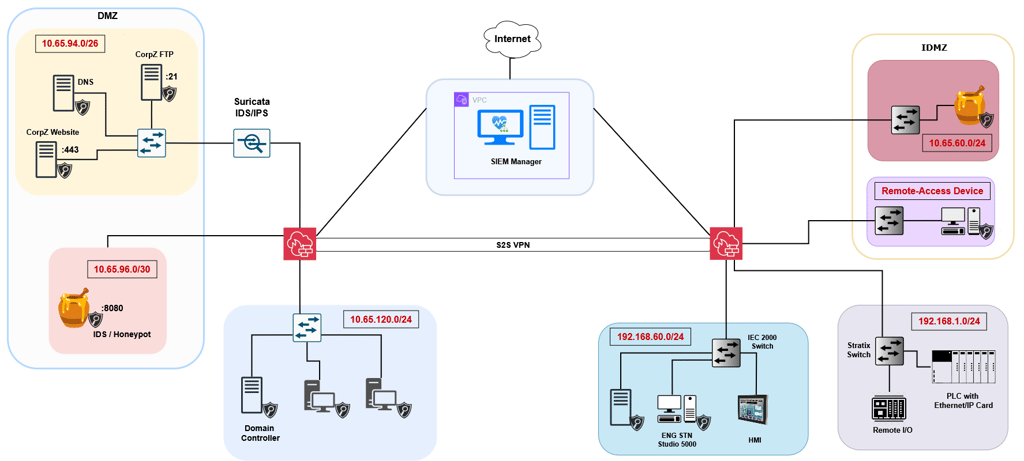
Re-viewed Network Topology