Domain Name System
Saif Chhipa
10/1/20243 min read
Domain Name System (DNS)
DNS is used to translate human-readable names (like xyz.com) into computer-readable IP addresses (like 1.2.3.4).
When we browse the internet, we search using names such as Amazon, Google, or Cloudflare. These names are resolved into IP addresses using the DNS server provided by your ISP, typically your home router or modem.
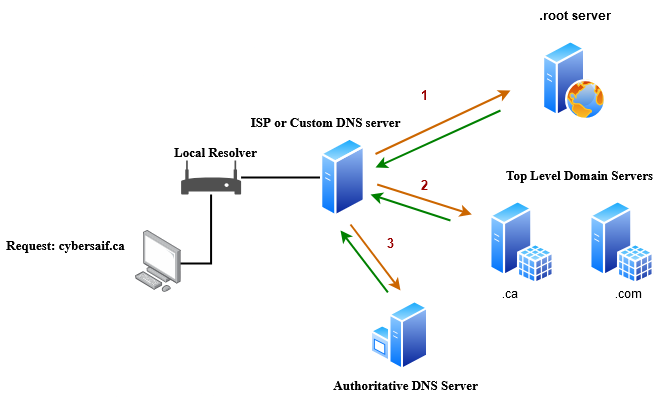
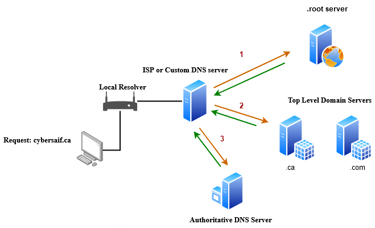
The request is processed like this:
When a PC needs to resolve a domain name, the local DNS resolver checks its cache. If it doesn’t have the answer, it forwards the request to a public DNS server like 1.1.1.1, 8.8.8.8, or whatever DNS your ISP provides.
The public DNS server checks its own cache. If the answer is not found, it forwards the query to a root DNS server.
The root server doesn't store actual domain records but knows who does. For a request like cybersaif.ca, the root server responds with the IP address of the Top-Level Domain (TLD) server for .ca.
The public DNS server then queries the .ca TLD server. This TLD server holds information about the registrar for cybersaif.ca.
The registrar is the organization (like Google Domains or AWS Route 53) where your domain is registered. They hold the records that map your domain name to your website’s IP address.
The DNS server then queries the authoritative DNS server, and receives the final IP address for cybersaif.ca.
Iterative vs. Recursive DNS Query
Let’s say a user wants to visit cybersaif.ca:
Iterative Query
In an iterative DNS query, the user sends a request to their local DNS resolver for the IP address of cybersaif.ca. If the resolver does not have the IP address, it will return the address of another DNS server instead. The user's client will then query this new DNS server, and this process will continue until it receives the correct IP address for cybersaif.ca, rather than another DNS server's address.
Recursive Query
In a recursive DNS query, when the user requests cybersaif.ca, and the local DNS resolver does not have the answer, it automatically queries another DNS server. If that server does not have the information, it will query yet another server. This process goes on until the correct IP address of cybersaif.ca identified.
Authoritative vs. Non-authoritative Responses
An authoritative response occurs when a reply to a query comes from an authorized DNS server. For example, if I purchase a domain name from Squarespace, Squarespace is an authorized DNS server. If I query "name.com" and receive a response from Squarespace, that response is considered authoritative. However, if the response to my query for "name.com" comes from my local DNS resolver or my ISP's DNS resolver, one that has cached the information, then that response is considered non-authoritative.
What is a Glue Record?
Glue records are special DNS records used for authoritative nameservers. For example, when querying "squarespace.com," your request first goes to the root servers and then to the top-level domain (TLD) server. Ultimately, it reaches the authoritative nameserver, which for Squarespace could be "ns0.squarespace.com."
When I try to visit Squarespace, my request goes to this nameserver, ns0. However, to resolve ns0, the parent domain first needs to be resolved, which is again squarespace.com. This creates a potential loop because the system needs to know the IP address of ns0.squarespace.com to resolve it. To prevent this loop, glue records are provided to TLDs, which include the IP addresses of nameservers like ns0.squarespace.com.
DNS Primary Zone vs Secondary Zone vs Stub Zone
In a Primary Zone, DNS records are stored with read/write permissions, allowing for the creation and modification of records directly on the primary DNS server.
A Secondary Zone holds a read-only copy of the DNS records that are transferred from the Primary Zone. It cannot be modified directly; any updates must come from the primary server.
Stub Zone: It holds a limited set of DNS records, also with read-only permissions. It typically includes records like the SOA (Start of Authority) and NS (Name Server) records to identify the authoritative servers for the zone.
Split DNS
Split DNS configuration involves setting up a DNS server that contains DNS records for internal services, these records are not available to the public.
To resolve queries for internal resources, like wk1.hr.int.adatum.com, you must configure your computer with an internal DNS server's address.
This setup helps protect sensitive internal resources by preventing public access to those domain names.
Types of DNS servers
There are several types of DNS servers that are used worldwide:
DNS root server
Authoritative name server
Non-authoritative name server
Caching server
Forwarding server
Resolver
DNS Records
Different DNS records are used for the DNS queries, which all have various tasks